Like email, passwords present a rare multitude of vulnerabilities and risks. As a means of verifying identity, and protecting resources, passwords are ineffective. They should have been replaced a long time ago, but instead great efforts have been made to keep them alive through a patchwork of defensive, partial solutions, thereby prolonging their role as a primary means of authentication. Many technologies have cropped up around passwords to address their many vulnerabilities, and most of these complementary systems, such as captchas, place an additional burden of effort on end users. Let’s discuss Captchas.
A Captcha’s purpose is to fool, or stymie, the automated tools used by hackers/attackers. These automated tools typically guess a multitude of passwords by quickly by running through huge volumes of password possibilities in hopes of guessing correctly. Unfortunately, password guessing tools are freely, and widely, available. They can run through every possible character combination within a configured, pre-defined scope, or use dictionaries of common passwords & phrases; or a little of both. The method of hammering away at login screens is generally known as ‘brute forcing’.
Captchas effectively rate-limit brute forcing attempts by requiring a user to decipher an image and type in the characters in the image into a textbox in addition to typing their password. The problem with captchas is that they are not only difficult for robots to decipher, they are also difficult and frustrating for non-robots, i.e. humans. As image recognition technologies become increasingly more capable of reading the characters nested in images, captchas will need to become proportionally more difficult to read in order to maintain their effectiveness, and therefore more frustratingly difficult for end users to decipher as well.
Another means of rate-limiting login attempts is temporary account lockouts triggered by multiple login failures. These are also inconvenient for end users because although lockouts can be configured to automatically expire after a period of time, during a lockout window, all productivity is lost. 15-, 30-, and 60-minute lockouts are 15-, 30-, and 60-minute productivity losses, respectively. And, when end users need to contact IT to request that an account be unlocked, the time spent in contact with IT is double loss in productivity; end user + IT.
In addition to the costs and inconveniences of these protective measures, passwords themselves are inherently problematic from a vulnerability standpoint because password strength mostly relies on the imaginations of end users. As a result, some passwords will be much more/less secure than others, but all will be trusted to provide the same level of access protection. Moreover, many passwords are constructed from something emotionally significant, and therefore memorable, to end users; family members’ names, birthdays, pets, sports teams, life events, etc. This makes them even easier to guess correctly.
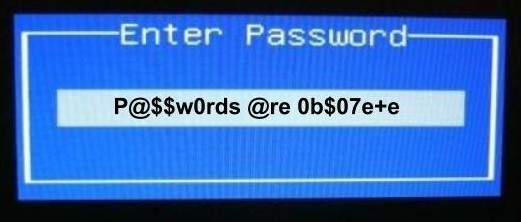
One way that IT and other service providers enhance the strength of passwords is by enforcing complexity requirements. To get around this, one common user behavior is to replace letters with symbols, e.g. ‘$’ for ‘s’, ‘7’ for ‘L’ and so on. These substitutions are easily guessed, and therefore an ineffective approach to obfuscating weak passwords. When password complexity rules are pushed to further extremes, end users bypass their human-memory limits by writing down passwords on post-it notes, or saving them in files on their computers. The end result is that the intended outcome of enhanced security is undermined. But, there is nothing wrong with end users knowing the limits of human memory. It’s human to remember things of emotional significance and to forget, or struggle, to remember pedestrian and unemotional things. To further illustrate human memory limits, try to remember what you ate for breakfast, or lunch, last Tuesday. It’s difficult, and it should be. Remembering every meal would be best described as a curse, not the gift of great memory.
If doors on homes were proportionally protective to the imaginations of their inhabitants, the situation would be absurd, and the onus of the protective effectiveness of doors would be quickly pushed back to door & lock manufacturers; where the responsibility is, and should be, assigned. I would much rather entrust a door or lock manufacturer to design protected entryways than rely on homegrown, imaginative [but perhaps more entertaining] booby traps.
Another weakness of passwords is that they can be easily shared, intercepted, and stolen. The entire world could know my passwords because they do not allow exclusive possession. The ‘something that you know’ factor by itself cannot restrict usage to an individual. Consequently, there is only one means of protecting passwords: keeping them secret and changing them often. Even then, passwords can be easily intercepted with phishing emails, or reading over someone’s shoulder at their desk, on the bus, or in any other setting where users type their passwords. In some environments, and for some users, passwords must be typed more frequently than others, e.g. Systems Administration/Administrators. The intent is to continually require re-authentication for enhanced security, but it also increases the number of opportunities to intercept passwords. Changing passwords often can mitigate some of these risks, but not eliminate them because new passwords are often similar to previous passwords- once again owing to the limits of human memory, rendering them more guessable, and undermining the intent of password rotation.
The concept of multi-factor authentication mitigates risks by adding things like tokens, phone calls, and SMS messaging so that logins do not rely on passwords alone, but these additional burdens are placed on end users, incurring further inconvenience and frustration.
Again, passwords, like email, are outdated and vulnerable. And also like email, the world is spending vast sums of cash to protect them. It would be more cost effective to stop investing in protecting them with additional layers of security and instead invest in replacing them altogether! Fortunately, there are options available to achieve this goal.
Smart cards are an excellent alternative means of achieving greater login/authentication security. These cards, or dongles, require physical possession, which means only a single person can possess & use them at once. Additionally, they are difficult to duplicate, and can be revoked if lost or stolen. They can also be combined with a PIN code to achieve multi-factor authentication, and can be integrated into workplace badges.
All systems have vulnerabilities, and smart cards are not a perfect solution, but they are more secure than end users’ imaginations, and because most workplaces already have electronic badge management systems, and require employees to badge into their workplaces, they do not increase the burden of effort placed on end users. Moreover, they can provide a single, centralized means of access control to both physical workspaces and computer systems.
If smart cards do not fit into your workplace or lifestyle, there are plenty of alternatives, such as biometrics, behavioral pattern recognition, geographic & location based access control (e.g. geo-fencing), and others. Regardless of what you choose, relying on the ‘something that you know’ factor will eventually require the introduction of a complementary technology to address this factor’s inherent weaknesses and vulnerabilities, and it may as well be something that replaces this factor rather than complements and prolongs its use.
In general, whenever a system or practice has so many flaws that significant portions of other industries (cybersecurity, password vaults) and technologies exist simply to address those flaws, the system or practice itself should be examined. At a certain point, the utilization of different access controls should be considered not as an add-on, but as a replacement. Captchas, re-captchas, and the near universally despised password complexity rules are not solutions. These are all means of enabling the continued use of an outmoded means of authentication & access control. More effective password alternatives exist, and they will hopefully supercede passwords in the near future instead of serving a limited role as complementary measures.